OPSEC Process. WRM specific facts about friendly intentions.
Online Privacy Through Opsec And Compartmentalization Part 3
Which of the following are parts of the OPSEC process.

. I dont know the parts of the opsec process. All of the following are steps in the OPSEC process EXCEPT. 1Identification of Critical Information.
The last part of the OPSEC process focuses on protecting sensitive information. Therefore the identification of critical information would be important to this process because OPSEC would want to protect the critical information first and foremost before attempting to protect any unclassified information. Analysis of threats application of appropriate countermeasures conduct vulnerability assessments.
Identifying critical information Analyzing threats to that information Examining vulnerabilities to those threats. It involves five steps. Which of the following are parts of the OPSEC process-Identification of sensitive information-Analysis of threats-Application of appropriate countermeasures-Conduct.
Match the five-step OPSEC process with the action associated with the step. The processes involved in operational security can be neatly categorized into five steps. Answered by wiki 19062021.
OPSEC is a process of identifying analyzing and controlling critical information indicating friendly actions associated with military operations and other activities. Which of the following are parts of the opsec process 1 See answer Advertisement Advertisement CrazyKitty7450 is waiting for your help. Display of associated vulnerability components C.
Measuring the amount of information that the adversary possesses. Answer Which of the following are parts of the OPSEC process. Tap again to see term.
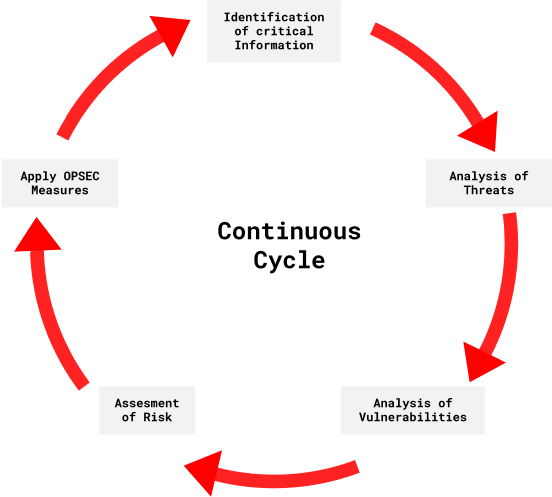
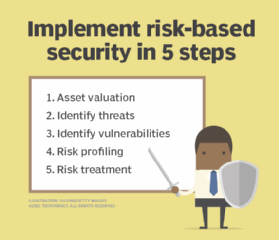
ALL OF THE ABOVE. Click card to see definition. 1 identify critical information 2 identify the threat 3 assess vulnerabilities 4 analyze the risk 5 develop and apply countermeasures.
Which of the following materials are subject to pre-publication review. Identification of system administrators. Which step in the opsec process requires you to look at your operation through the eyes of an adversary.
Add your answer and earn points. Operations security OPSEC is a process that involves the identification and protection of unclassified critical information or processes that can be used by a competitor to gain real information when pieced together. Click card to see definition.
Click again to see term. Which of the following are the process steps of OPSEC. Advertisement Advertisement New questions in Computers and Technology.
Choose all that apply. Analysis of threats application of appropriate countermeasures conduct vulnerability assessments Most relevant text from all around the web. Which of the following are parts of the OPSEC process.
Tap card to see definition. Click again to see term. The sun is the center of the universe.
Each correct answer represents a part of the solution. Tap card to see definition. The OPSEC process has five steps which are as follows.
The earth rotates around the moon. What is the effect of the mission the cost of avoiding risk how will adversary benefit from. Analysis of threats Step 2 Deals with identification the adversaries their intent and their capability to use the information against an organization.
Identify your sensitive data including your product research intellectual property financial statements customer information and employee information. The following should be considered when assessing risk. Identifying information vitally needed by an adversary which focuses the remainder of the OPSEC process on protecting vital information rather than attempting to protect all classified or sensitive unclassified information.
Which of the following are parts of the OPSEC process. This will be the data you will need to focus your resources on protecting. Identify critical information identify the threat assess vulnerabilities analyze the risk develop and apply countermeasures are parts of the OPSEC process.
The OPSEC process includes the following five steps. Which of the following is required to access classified. Tap card to see definition.
Any step in the OPSEC process may need to be revisited at any time. Click card to see definition. Once we identify the threats we can study their Techniques Tactics and Procedures TTPs.
Click card to see definition. The OPSEC process is most effective when its fully integrated into all planning and operational processes. Identifying critical information identifying the threat assessing vulnerabilities analyzing the risk developing and implementing countermeasures is part of the OPSEC process.
Tap again to see term. According to Ptolemys model of the movement of celestial bodies A.
Tryhackme Red Team Opsec Write Up Summary Infosec Cafe

What Is Operational Security The Five Step Opsec Process Securitystudio
0 Comments